
Snovasys Penetration Testing Expertise || PENETRATION is a method of testing in which the areas of weakness in the software systems in terms of security are put to test to determine, if ‘weak-point’ is indeed one, that can be broken into or not.
Penetration testing tools are used as part of a penetration test(Pen Test) to automate certain tasks, improve testing efficiency and discover issues that might be difficult to find using manual analysis techniques alone. Two common penetration testing tools are static analysis tools and dynamic analysis tools. Veracode performs both dynamic and static code analysis and finds security vulnerabilities that include malicious code as well as the absence of functionality that may lead to security breaches.

For example, Veracode can determine whether sufficient encryption is employed and whether a piece of software contains any application backdoors through hard-coded user names or passwords. Veracode’s binary scanning approach produces more accurate testing results, using methodologies developed and continually refined by a team of world-class experts. And because Veracode returns fewer false positives, penetration testers and developers can spend more time remediating problems and less time sifting through non-threats.
Performed for: Websites/Servers/Networks
How is it Performed?
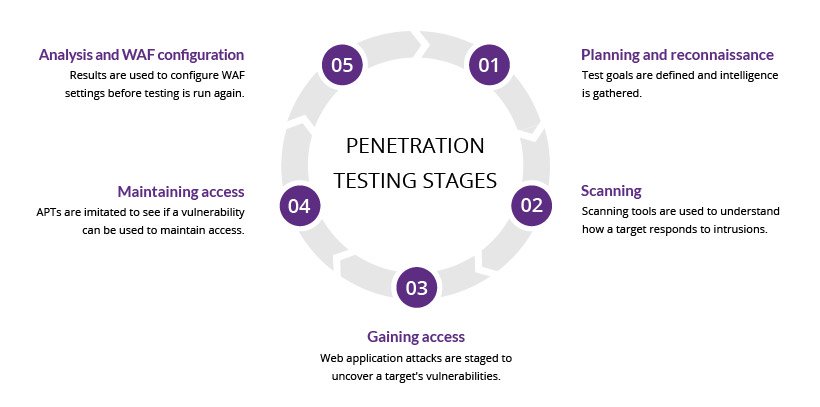
Step #1. It starts with a list of Vulnerabilities/potential problem areas that would cause a security breach for the system.
Step #2. If possible, this list of items is ranked in the order of priority/criticality
Step #3. Devise penetration tests that would work (attack your system) from both within the network and outside (externally) are done to determine if you can access data/network/server/website unauthorized.
Step #4. If unauthorized access is possible, then the system has to be corrected and the series of steps need to be re-run until the problem area is fixed.
Who Performs Pen-testing?
Testers/ Network specialists/ Security Consultants perform Pen-testing.

Who Performs Pen-testing?
Testers/ Network specialists/ Security Consultants perform Pen-testing.
Note: It is important to note that pen-testing is not the same as vulnerability testing. The intention of vulnerability testing is just to identify the potential problems, whereas pen-testing is to attack those problems.
Good news is, you do not have to start the process by yourself – you have a number of tools already available in the market.
For more information with sample..Click Here

